The code compiles. All the tests pass. The staging environment is healthy. Yet once per day a few servers in the production fleet mysteriously observe a crash with an error message that makes no sense – unreachable code has been reached, we have taken 9 items out of a collection that can only hold 8, or similar. Welcome to the world of rolling your own synchronization primitives.
Author: Sander Saares
Memory allocation is the root of all evil, part 2: Rust
A previous article illustrated how algorithms written in naïve C# can easily underperform due to being sloppy with memory allocations. It is a common assumption for engineers moving from the .NET world to the Rust world that this problem is automatically solved by Rust because "Rust is more efficient". Alas, this is not the case. … Continue reading Memory allocation is the root of all evil, part 2: Rust
Structural changes for +48-89% throughput in a Rust web service
Optimizing algorithms can be demanding work, requiring a fine-grained understanding of what the processor is doing, involving many repeated measurement and adjustment iterations, depending on a theoretical understanding of computer science principles and mathematics, requiring specialized tooling and the knowledge of how to use it. This article is about something completely different. We will take … Continue reading Structural changes for +48-89% throughput in a Rust web service
You do not need multithreading to do more than one thing at a time
As hardware gets faster and more capable, software keeps getting slower. It is remarkable how inefficiently typical apps use the capabilities of modern processors! Often this means an app is doing only one thing at a time when it could do multiple things simultaneously, even on a single thread. This article explores a technique for … Continue reading You do not need multithreading to do more than one thing at a time
Why is std::pin::Pin so weird?
Values of certain Rust types need to be pinned, which prevents them from moving in memory. This is expressed via the std::pin::Pin wrapper type and is typically encountered in the form of a function accepting Pin<&mut T> instead of &mut T. Pinning makes using many “normal” programming techniques difficult and has strange side-effects that do … Continue reading Why is std::pin::Pin so weird?
AI will change the world – but not through the AI products of today
The rising skepticism about the value generated by AI is justified. The AI products on the market today are only the first step toward meaningful transformation. We must push forward to cover the rest of the critical path while momentum lasts. Existing AI products are designed to find, recognize and synthesize information There is a … Continue reading AI will change the world – but not through the AI products of today
Does Rust have an advantage if memory-safety is not an advantage?
Rust is best known for its memory safety features. At the same time, most web services today are already built using memory-safe languages such as Java, Python, Go or C#. Are there still compelling reasons to use Rust when the competing language is equally memory-safe? Perhaps there is a performance difference? Let's test the hypothesis … Continue reading Does Rust have an advantage if memory-safety is not an advantage?
Memory allocation is the root of all evil
Most production code is written without its performance being a goal, using "typical" coding patterns for different languages. These patterns tend to be exemplified in articles, official documentation and tutorials. Typical code allows you to get things done rapidly by making use of powerful and flexible language features and APIs. However, typical code is not … Continue reading Memory allocation is the root of all evil
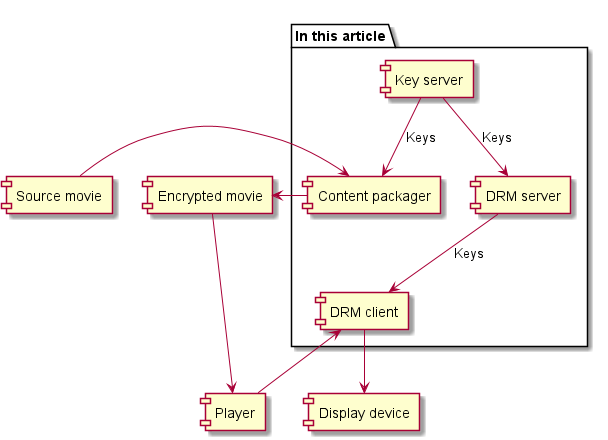
DRM is not a black box, part 4: key management
DRM merely enforces policy and does not own keys. Historical key managament approaches leave it all in the care of the DRM vendor, leading to major lock-in and maintenance headaches that can require solution re-architecting when DRM vendors are changed or added. A modern solution architecture separates key management from DRM and enables flexible integration … Continue reading DRM is not a black box, part 4: key management
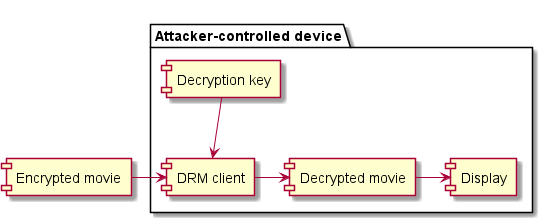
DRM is not a black box, part 3: secure playback
DRM clients are different but same. Security of DRM relies on keeping secret the cryptographic keys that protect content. The DRM client is the only component on the viewer's device authorized to handle these keys. In the DRM security model the viewer is the attacker which means that a DRM client operates under very difficult … Continue reading DRM is not a black box, part 3: secure playback